Many people assume that an email is safe if it comes from someone they know. That’s a dangerous assumption. The most lethal emails we see clients open did, in fact, come from someone they knew. That’s part of the vicious cycle of phishing emails. They steal your email password and then try to do the same to everyone you’ve ever sent an email to. It’s not unusual to see a successful phishing scam circulate for weeks among local law firms. But you can learn to spot the tell-tale signs of a phishing scam which arrives in your inbox as something shared from a friend or associate.
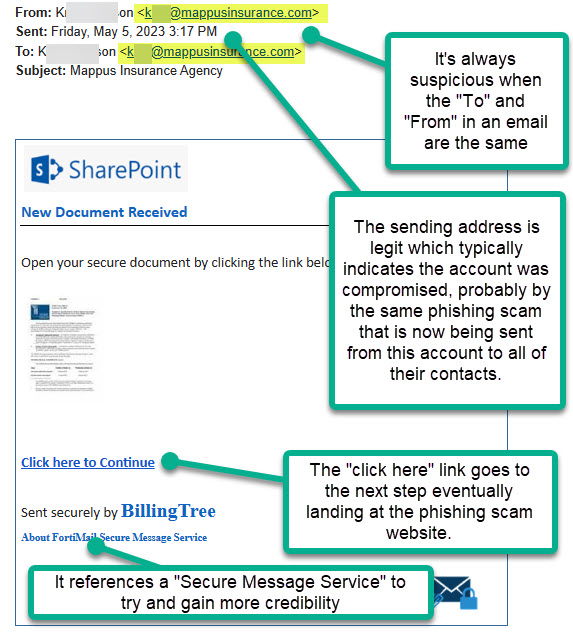
Look for anything unusual in the format or wording of an email. Does it look like emails you have previously received from this person. Is the wording or punctuation off. Was the email addressed to you or does the “To” field show an address other than yours. Phishing emails commonly show up as links to popular services like SharePoint, OneDrive, Google Drive, Dropbox, Docusign, etc…Although these are valuable services when used legitimately, they’re also very often abused for ill.
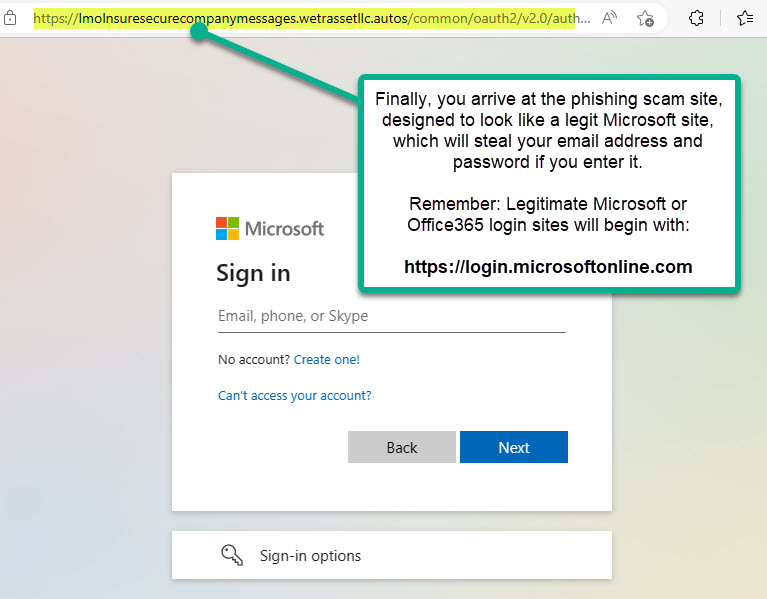
Ask yourself the most common sense question of all: “Why did they share this with me?” If you’re being sent a file you didn’t request you need to treat it very carefully. You may have just stepped into a minefield so stop and think before your next step. The old saying “curiosity killed the cat” can also translate to “curiosity allowed ransomware to kidnap all of my company’s files and shutdown our office.” One extra mouse click is all it takes. Remember that in phishing scams the ultimate prize is your password. NEVER EVER NEVER give up your password unless you’re 100% certain it’s required. 99.9% of the time, a request for your password will be a scam.
We filter our client’s emails for spam and phishing scams and have additional security safety nets for the few that sneak through. We also plea with our clients to forward anything suspicious to us for inspection if they have any doubt. But ultimately the user is the last line of defense. Arm yourself with knowledge and a good suspicious set of eyes.
In the provided screenshots the phishing email showed up to our client from someone they do business with. It was posing as a shared file sent via Microsoft’s SharePoint service. It uses several masking techniques to evade security but ultimately lands on the phishing scam website and asks for your email address and then your password.