How to Avoid Email Scams (Seriously—Read This)
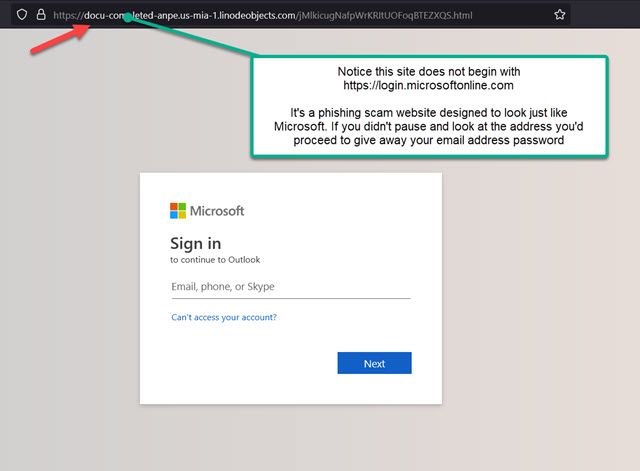
Scammers are getting slick. One of their favorite tricks is setting up fake Microsoft sign-in pages that look almost identical to the real thing. Their goal? To get you to hand over your email password without thinking twice.
If you don’t read anything else in this guide, remember this one critical rule:
👉 Never enter your work email password into any site that doesn’t start with:
https://login.microsoftonline.com
Yes, that exact URL—and nothing else—is the only thing that matters. It doesn’t matter how convincing the page looks, how real the logo appears, or how official the email seemed. If the address bar doesn’t start with that exact URL, it’s a scam.
Quick Notes:
- These instructions are specific to Microsoft 365 email accounts. (If you’re using Gmail or another service, the advice will differ.)
- The address can have more stuff after that, but it must start with
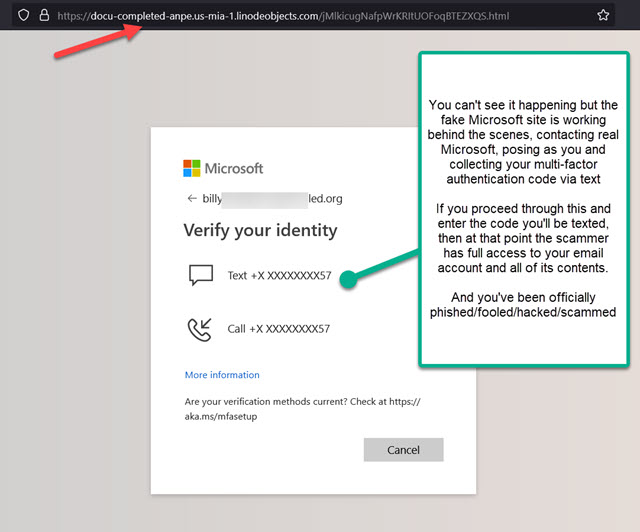
https://login.microsoftonline.com. - MFA (multi-factor authentication) is great—but it won’t protect you if you hand your code over to a fake site.
- Many scam emails come from people you do know—because they already got fooled and their accounts were hijacked.
Bottom line: Don’t trust the design. Don’t trust the sender. Trust the address bar.
One wrong click and you’re not just compromising your inbox—you’re potentially putting your entire company at risk.
Stay sharp. Scroll down to see what the real Microsoft login page looks like.
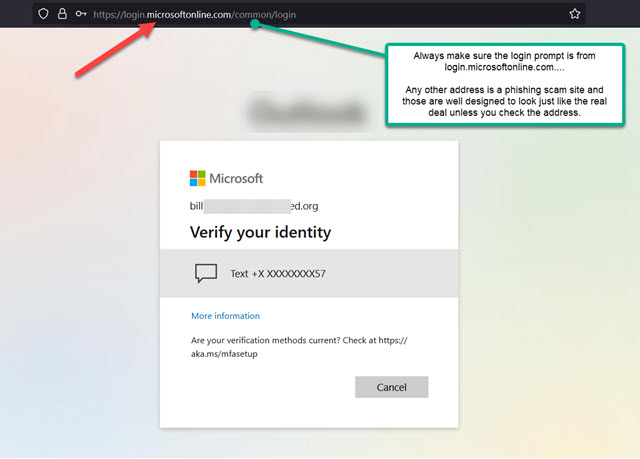
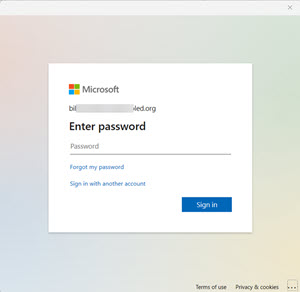
But unfortunately, it does get a little more complicated. Microsoft apps like Outlook, Teams, OneDrive, Word and Excel can also prompt you for logins so those apps can connect to Microsoft cloud based services. In that case, you’ll get a smaller login box without any address at all. All the examples below are legitimate and came from a variety of legitimate Microsoft apps. Notice there’s no address bar at the top – because these login boxes are being generated by the Microsoft apps.
Bottom line: If you have any doubt stop and reach out to us so we can confirm.
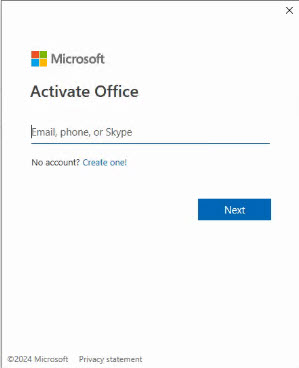
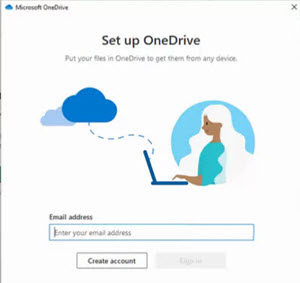
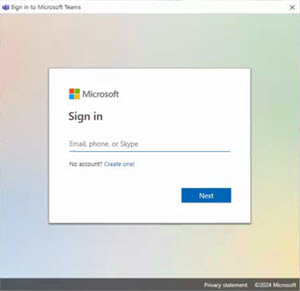
Below is an email recently received from a legitimate contact who had been scammed into giving up their own password. Unfortunately, this scam succeeded in convincing one of our customers to give up their password. On closer inspection, you can see how it would have been easy to get fooled — if you weren’t looking in the right places.
On first glance, the email looks somewhat convincing. It came from someone familiar to the recipient. It had the recipient’s name in the body of the email. The wording is suspicious, as is the case in many scam emails. But without reading it closely, that might not stand out. The “review” PDF file opens to a third-party site which should have been the first big red flag. But you’d have to look at the website address to realize that. When it then opens to a (fake) Microsoft login page, that should have set off major alarms. A logical first question would be: Why do I have to sign into my email account to open this PDF file that I didn’t even ask for to begin with? And here’s where our earlier most important thing to remember could have saved the day. The address of the (fake) Microsoft login page was obviously not legitimate Microsoft. Not even close. ALWAYS check the address of any website before you start typing your email password. Almost always, it will be clearly evident whether it’s legit Microsoft or some fake phishing scam site trying to steal your password. STOP before you TYPE.
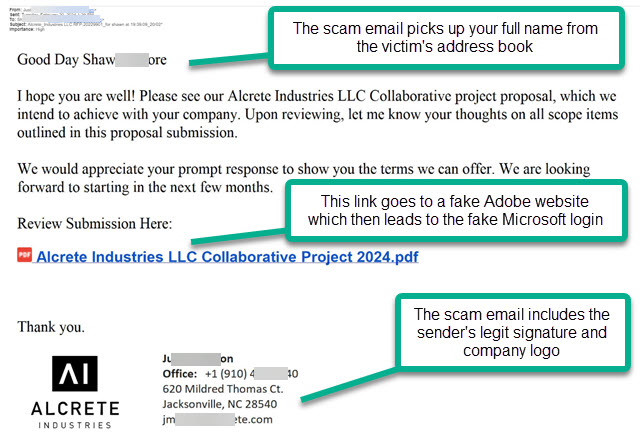
The first leg of the scam takes you to a website posing as legit storage for an Adobe PDF file you’re asked to review.
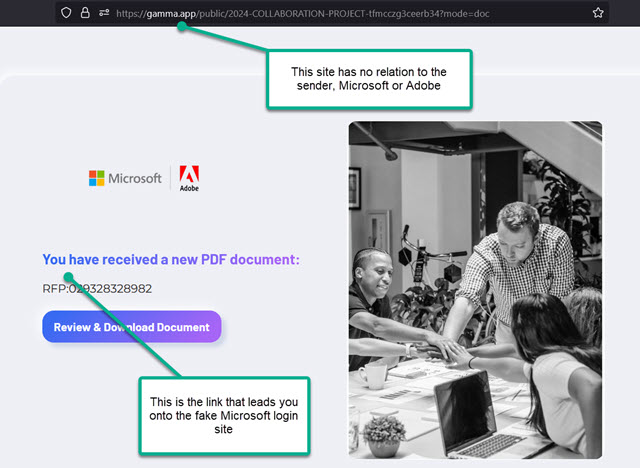
From there you’re taken to the fake Microsoft login page. This is where you can save yourself by simply looking at the address at the top of the page. If you rush on past and start entering your info, you’re well on your way to being scammed. If you enter your email password and authentication code, you’re fully scammed.